Everything you know about passwords is probably wrong
The modern internet has taught us some bad lessons about password use
Hello friends,
Happy Valentine’s day !
Today we’re discussing passwords. I will be showing you why some current ‘password strength’ metrics are dumb and teach us the wrong lessons. Then I’ll show you what a good password looks like, how to remember it and some other password best practices.
It goes without saying that you should not use any of the examples I show today as your personal password.
For the sake of argument, let’s assume that I’m making a new Google account today.
So I’m going to try to create a pretty good password.
I’m going to make it long (Google suggests at least 12 characters).
I’m going to add in some numbers and symbols to make it even harder to guess.
I also need to make it easy to remember, so I don’t get locked out of my account.
I’m going to also check this password’s strength to make sure the hackers won’t crack it and see all the super-secret Taylor Swift fan-fiction I like to write in my free time.
*thinking noises*
I got it! Let’s check the strength.
Google’s top 2 results for “check password strength” are
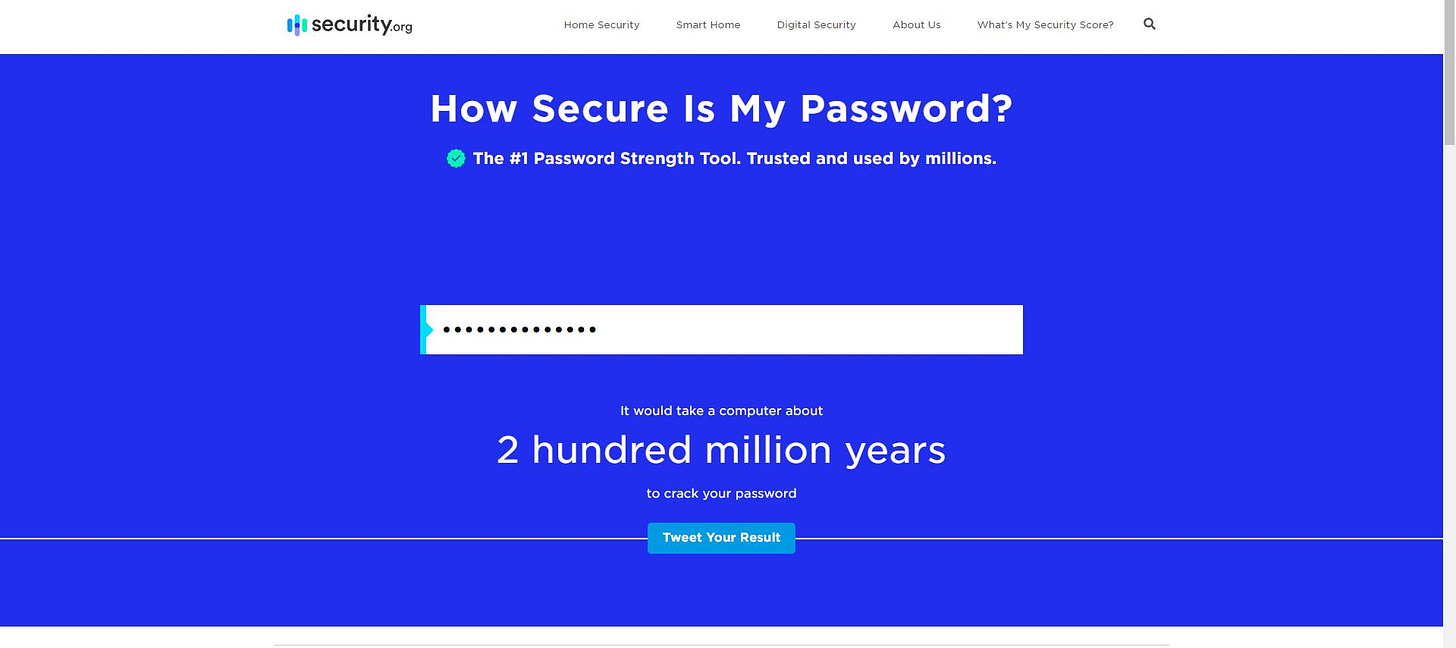
Security.org where I get the following result :
200 million years for a hacker to crack my password! That sounds great, super-secure.
I’ll reveal the password I created a little later, but for now let’s check on what the 2nd option has say about it.
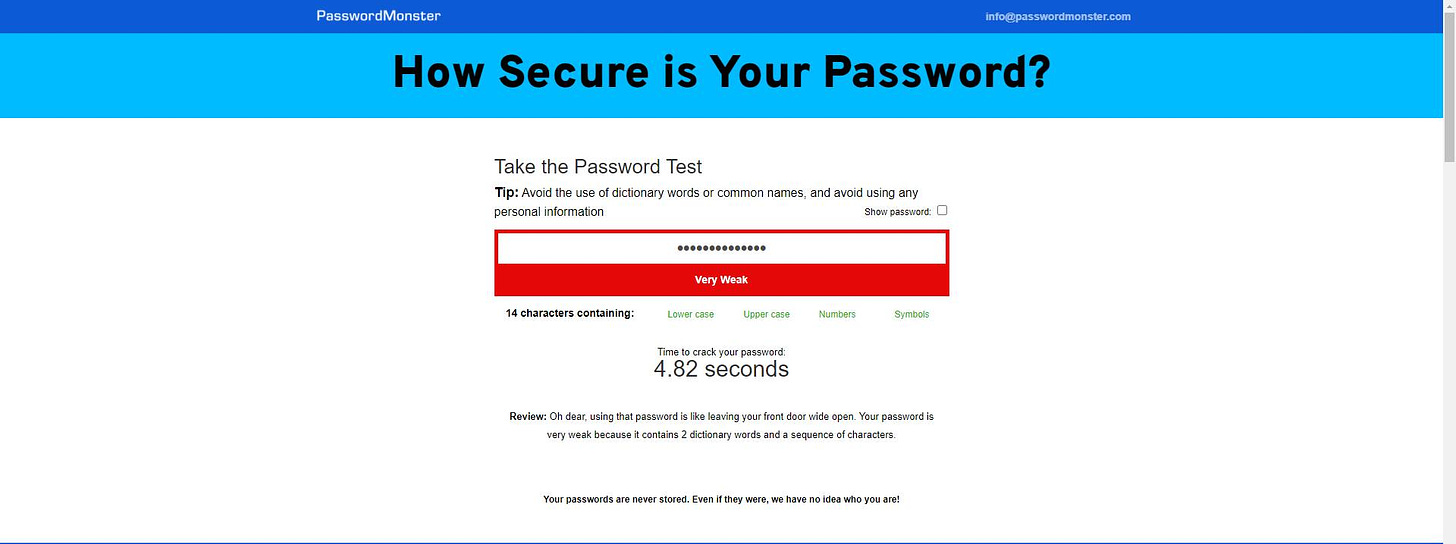
PasswordMonster.com where I get the following result :
Well, that’s not good. Not good at all. My password would be cracked in under 5 seconds.
How can this be ? Why the discrepancy between the two?
Let’s do some reflection, maybe we can figure it out.
Most websites and services don’t know your actual password.
Whenever you go to a website - you are typically asked to provide your login credentials: A username and a password or PIN.
This happens even if you don’t see the login screen. In this case, your browser or phone just store the credentials and use them when you access the website or app.
Logically, that means that the website must have your password stored somewhere to check that you’ve used the correct one.
The truth is that the website stores something, but it’s usually not your actual password.
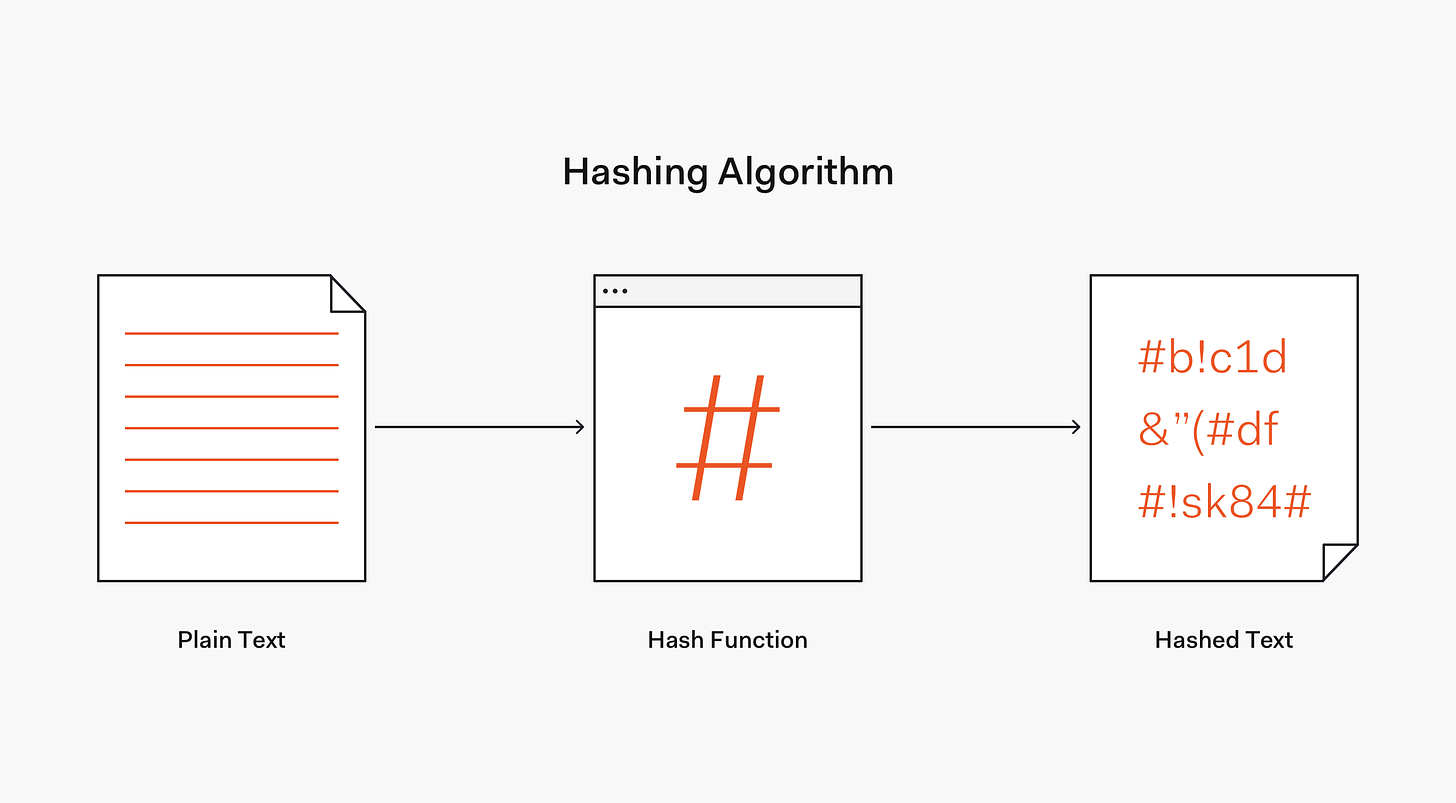
What the website usually stores is something that looks like this :
BBBFB9EE6E99C269DFCDEFE7E2D1A919CD3DC023D3A6090148DC87D915A38D00
That string of letters and numbers is called a Hash, and it is fundamental to password security. (it’s also pretty fundamental to all the cryptocurrency stuff - but that’s a topic for another day).
So what is a Hash and what is it useful for ?
A Hash function is a mathematical function that has 2 very interesting features.
It is very easy to get from the input to the output.
It is very hard, almost impossible, to reverse engineer. If you have the output, you cannot determine what the input was.
So why is this good for passwords ?
If websites or apps knew your human-readable password (usually called clear text or plain text) that could be bad for you. People inside the company could access your account or even hackers that get access to your user data very easily.
So instead of storing your password as plain text, it will be stored as a hash. Whenever you login, the website will quickly turn the password you write in your login screen into a hash and compare it to the hash they have in their database. If it’s a match you’re logged in, if not you’ll get a “Password is incorrect” message.
And because it’s very easy (read cheap) to get from a plaintext password to a hash this makes the login process very quick and relatively safe.
How can hackers crack my password if this hash thing is so good ?
The first thing to note is that because most apps/websites store password hashes it means that if a malicious threat actor gets their hands on our credentials, it will most likely be a hash.
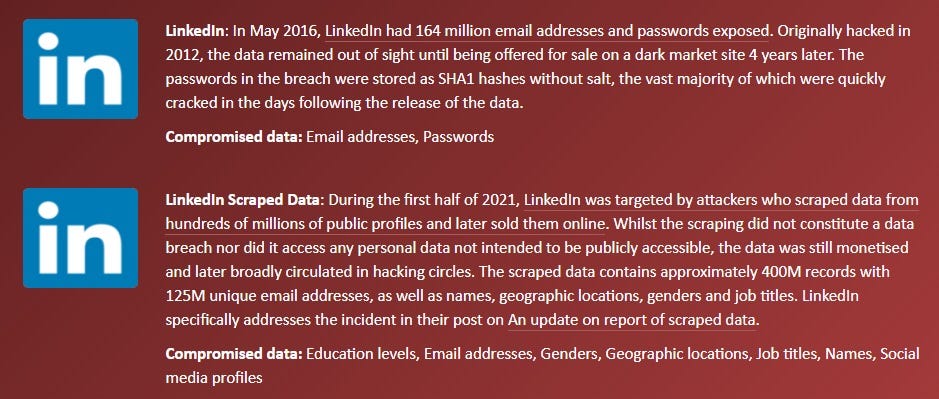
In last week’s post, I showed an example of an email address that was compromised in a LinkedIn hack from 2012. Attackers got their hands on that user’s encrypted password and could take a shot at cracking it.
But because password hashes are hard to reverse engineer what they would try to do is generate a plaintext password, convert it to a hash and compare the resulting hash to the password hash they recovered from the LinkedIn hack.
There are 2 main ways password crackers could try to find that password.
Please note that there are plenty of ways bad actors will steal credentials - these are typically scams (commonly referred to as “social engineering”). Today' we’re discussing cracking passwords, not obtaining them through other means. Social engineering will be the subject of another post - for now just remember not to click on sketchy links.
First method is called a “Brute Force” attack.
As the name might suggest, the Brute Force attack will systematically try all possible combinations until it gets the right result.
Something like “a” then “b” then “c” …. “aa” … “ab” … “ac” … until they finally see a match. To get an idea about how long this method could take, let’s finally reveal what the password I initially created was.
Password is : Reputation!123
It’s 14 characters long. It has a capital letter, a symbol, and some numbers.
(just like most Apps/services suggest)
Somebody brute-forcing this password would have to go through 4,517,347,060,908,032,000 combinations. The time this can take really depends on the computing power the attacker has at their disposal, but it’s not a stretch to say that the estimate that the first website gave us (200 million years) is, if not realistic, at least plausible (i.e. more time than my password is realistically worth).
So it’s safe to use, then?
Not so fast. Passwords are something we have to remember. And to make it easier to remember I used a recognizable word and a very intuitive string of numbers at the end. Attackers are keenly aware of how long brute-force attacks can take, and they also know that our brain will have trouble remembering complex strings, so they have refined their attacks to account for this.
Enter method #2 : the Dictionary attack.
This type of attack is pretty self-explanatory. Instead of trying any random combination of letters, our password cracker will, instead, try known words that humans can remember. This makes their life much, much easier.
The English dictionary has around 170,000 words. We can safely multiply that number by 1000 to account for any linguistic shenanigans (like a cheeky spelling of the word ‘R3put@t10n’) and the resulting 170,000,000 words are still orders of magnitude below the 4.5 billion billion tries the brute-force attack requires.
This is why the second website gave us such a poor rating on the same password (5 seconds to crack). A dictionary attack will obliterate this password much, much faster because - despite following several best-practices we’ve been taught over the years - it is very vulnerable to such an attack.
What do I do about my passwords, then ? Will hackers just get into my account ?
First thing’s first - you should probably take a look at how secure your passwords are.
If your passwords follows a similar pattern to the one I used : “word-symbol-number” it’s probably very insecure.
It’s also a good idea to get a feel for what the best practices are on a regular basis. I plan on making a yearly password guide in this newsletter. It probably feels unpleasant to have to go through this process regularly, but the unfortunate reality is that the bad guys are refining their methods every day and that means so should we.
So make sure to subscribe for free so you don’t miss that post at casualcybersecurity.substack.com
PasswordSSS. Plural.
You should never - under any circumstances - use the same password for multiple services especially the ones connected to your credit card.
This is called “credential stuffing” and is a big reason why hackers can break into your accounts with a cracked password.
So far we’ve talked about how many times hackers have to try a password in order to crack it - but we haven’t addressed the fact that Google, Instagram, Amazon, your bank etc. will lock you out if you have too many unsuccessful attempts to log in.
For all their faults, the big tech companies put some mitigation measures in place to ensure that your account is harder to access maliciously, but
They are not fool-proof. See Twitter leaks, Facebook leaks, Linkedin leaks.
Smaller or niche players tend to do a worse job securing their users’ data because they have fewer resources to deploy.
So it’s precisely the hypothetical Taylor Swift fan-fiction forum that is the weakest link in your security perimeter. If you re-use passwords, then an opportunistic attacker can link your email address to your other accounts and do some real damage.
To sum up what we covered so far.
Passwords should be long (to deter Brute Force attacks).
Passwords should not use a known word (to deter Dictionary attacks).
I should have a unique password for each different app or service I use.
Please take note that using “password.instagram” isn’t a clever trick. What do you think that user’s gmail password is ?
These 3 conditions will make your password management very inconvenient.
So how do we solve the Convenience vs Security Dilemma ?
Password Managers
Password managers solve all of these problems. Paid options exist, but for most folks the free options are more than enough.
If you’re struggling with choice paralysis BitWarden is my suggestion.
Password managers will suggest the strong and complex passwords and remember them for you. (The type of passwords that look like your cat slept on the keyboard).
So, instead of remembering multiple complex passwords for all your apps and services, you only have to remember a master password to access and use the Password Manager on your device (yes, you can have the Password Manager on multiple devices and/or browsers).
One (strong) Password to rule them all
So we need to craft a strong password that we can remember, while also making it very hard to crack.
Here’s the trick I recommended to my mom:
Think of a song you know the lyrics to. Sample :
We're happy, free, confused, and lonely at the same time
Let’s turn this into a password :
We already know the words, all we need to remember is the order of the symbols.
But the problem with that password is that it uses words. There’s a higher complexity involved in cracking it because it’s long - but it is still vulnerable to a more sophisticated dictionary attack.
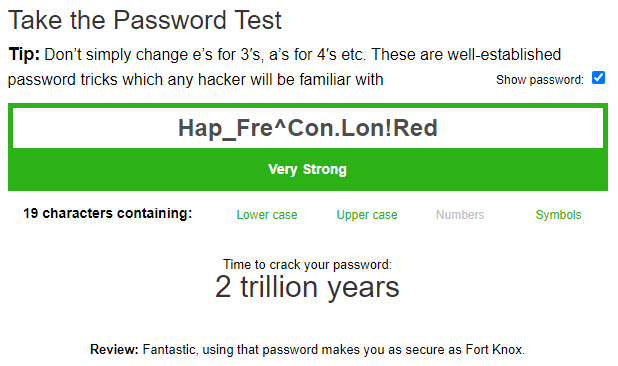
So instead, let’s just take the first 3 letters from each word and see what we get :
Did you notice that this option is a shorter, but stronger password ?
What if I don’t need a password because I use FaceID/Fingerprint?
Glad you asked !
Biometrics and Multi-Factor Authentication (MFA) or Two-Factor Authentication (2FA) is what my next post will be about. Make sure you subscribe for free so you don’t miss it !
Aaaaand we’re done with this week’s post. Thanks for reading. Drop me a like or a comment if you enjoyed this post.
For now, stay safe and sound !
CCS




Very interesting article. I started to educate myself about cyber security lately. I think it's a must for everyone using internet actually.